Introducing text2iam: Generate AWS IAM Policies with GPT-3

Writing AWS IAM policies can be split into 50% figuring out what you need it to do and 50% figuring out how to take what you can describe and translate into the AWS IAM policy schema.
Instead of searching different phrases like "S3 read only access policy" on Google, we put together an experiment called: text2iam — the easiest way to generate and explain AWS IAM policies by using OpenAI GPT-3 under the hood.
With text2iam, you can describe the policy you’d like to create using natural language and it will generate the corresponding AWS IAM policy in JSON.
Here are some examples:
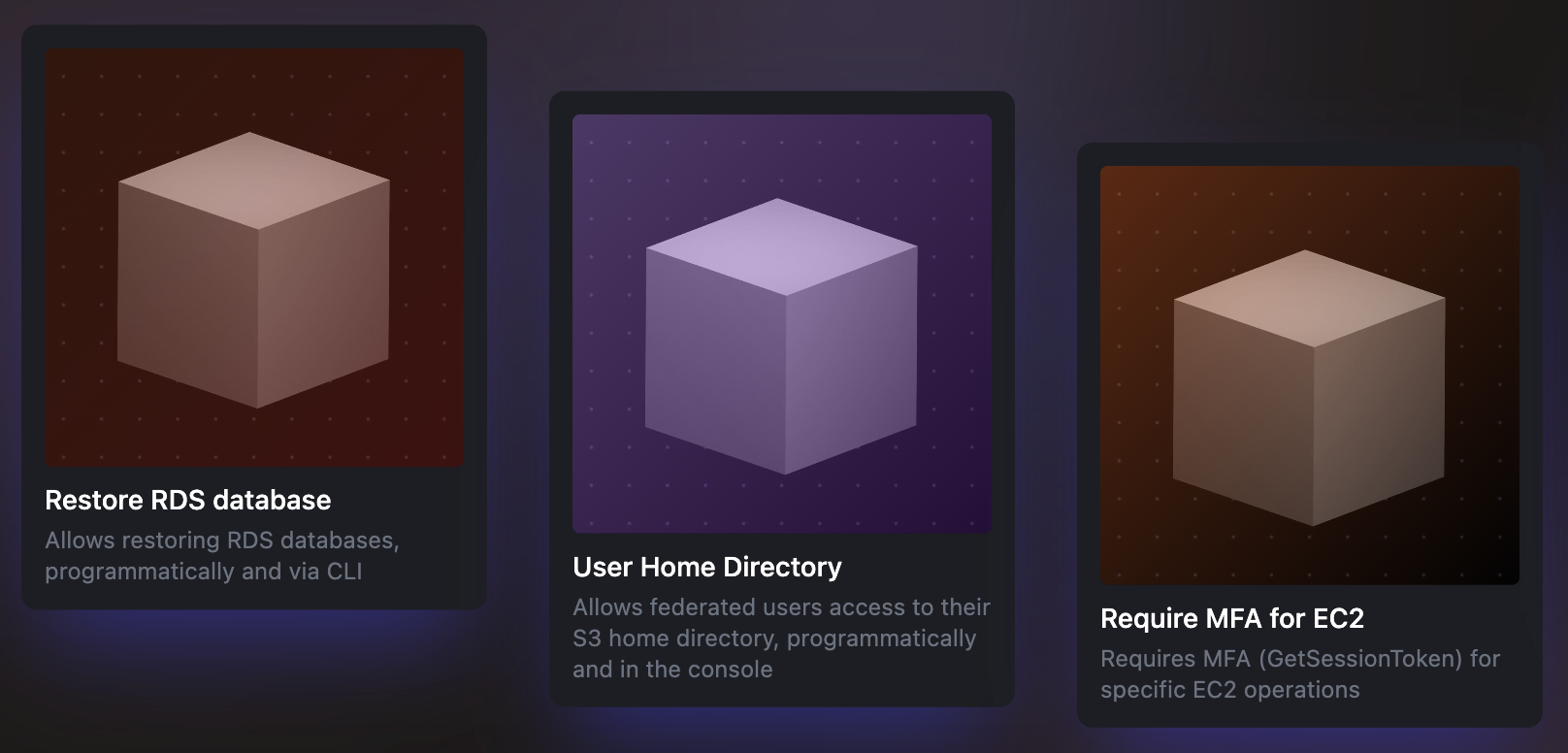 Example AI generated IAM policies
Example AI generated IAM policies
While we were developing this experiment and validating with test cases, we realized that being able to explain existing AWS IAM policies could be just as helpful as creating new ones.
You can now convert:
Allows users to rotate their own credentials (api keys, passwords)
Into an AWS IAM policy like:
{"Version": "2012-10-17","Statement": [{"Sid": "AllowUserToRotateCredentials","Effect": "Allow","Action": ["iam:CreateAccessKey","iam:UpdateAccessKey","iam:DeleteAccessKey","iam:CreateLoginProfile","iam:UpdateLoginProfile","iam:ChangePassword"],"Resource": "arn:aws:iam::*:user/${aws:username}"}]}
Obvious disclaimer: like all AI generated work, it’s not going to be perfect every time. You should review the policies before putting them in production.
Let us know if you have any thoughts or feedback on text2iam and the rise of AI-assisted security policy generation. Mention us @indent on Twitter, or email us at [email protected].
Interested in talking with our team about the security of your AWS account? Feel free to schedule time that works for you: indent.com/demo/request

