Indent Sunset Notice
We started Indent with the goal of helping teams protect what matters most. Our customers have secured everything ranging from customer data and production infrastructure to everyday business software — all without slowing down their team’s velocity.
After careful consideration, we’ve made the very hard decision that Indent will shut down in the coming months and we’ll help customers transition and continue working towards this shared goal.
Teams will be able to make requests until 12pm PST, Monday, July 15th, 2024, when services will be sunset. Audit logs will be available until Friday of that week after (July 26th) when we’ll start data deletion process.
We’d like to thank everybody who used Indent, from the early-stage startups securing access on day one to the teams of hundreds using Indent to secure mission-critical resources.
— Indent Team
Move fast and fix things.
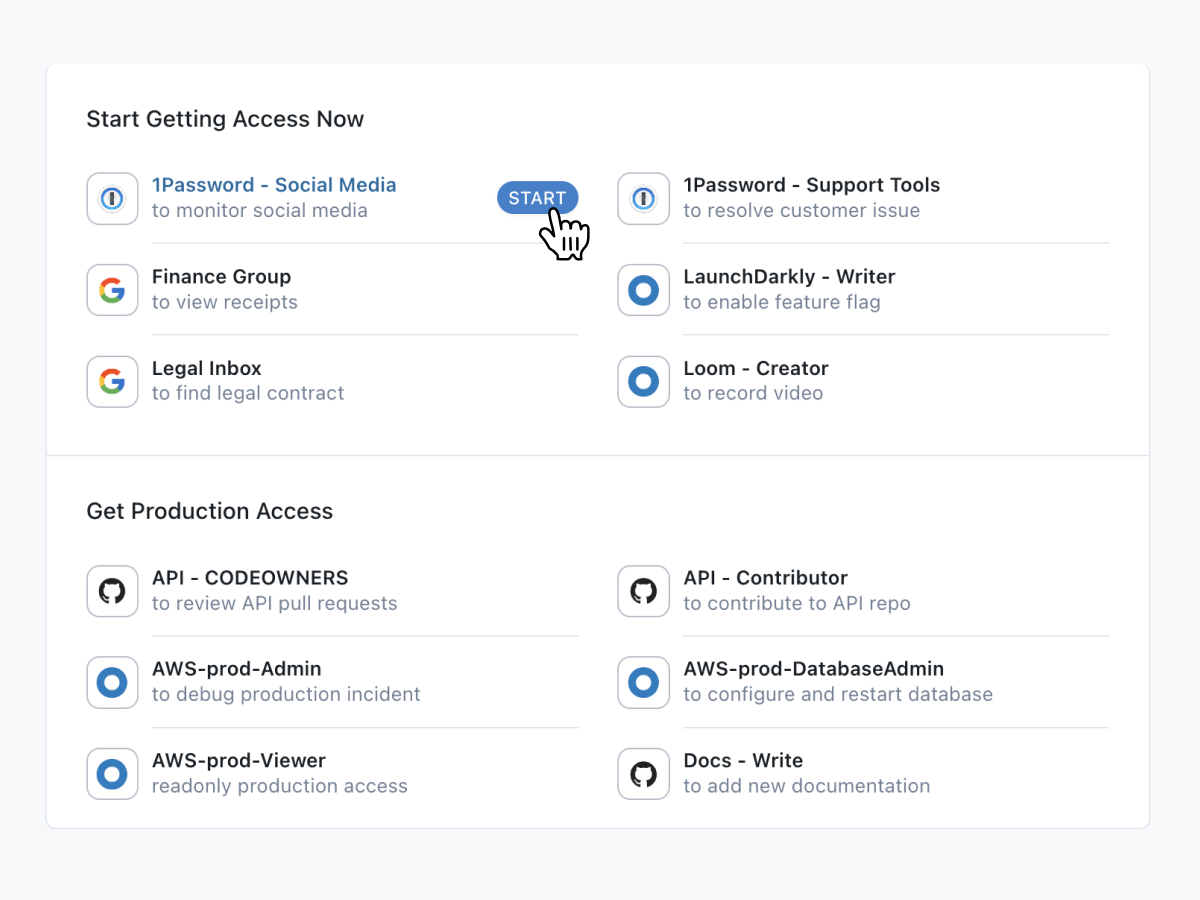
Engineers get production access instantly in the middle of the night when they're on-call
On-Call Auto Approval Bot
Approved for 12 hours
Peace of mind from unblocking your team to do their best work.
From early startups to the world's best engineering teams, helps companies move faster.
Manage your cloud, apps, and customer data in one place.
- For Engineers: get production access instantly from Slack or grant temporary GitHub access to a contractor
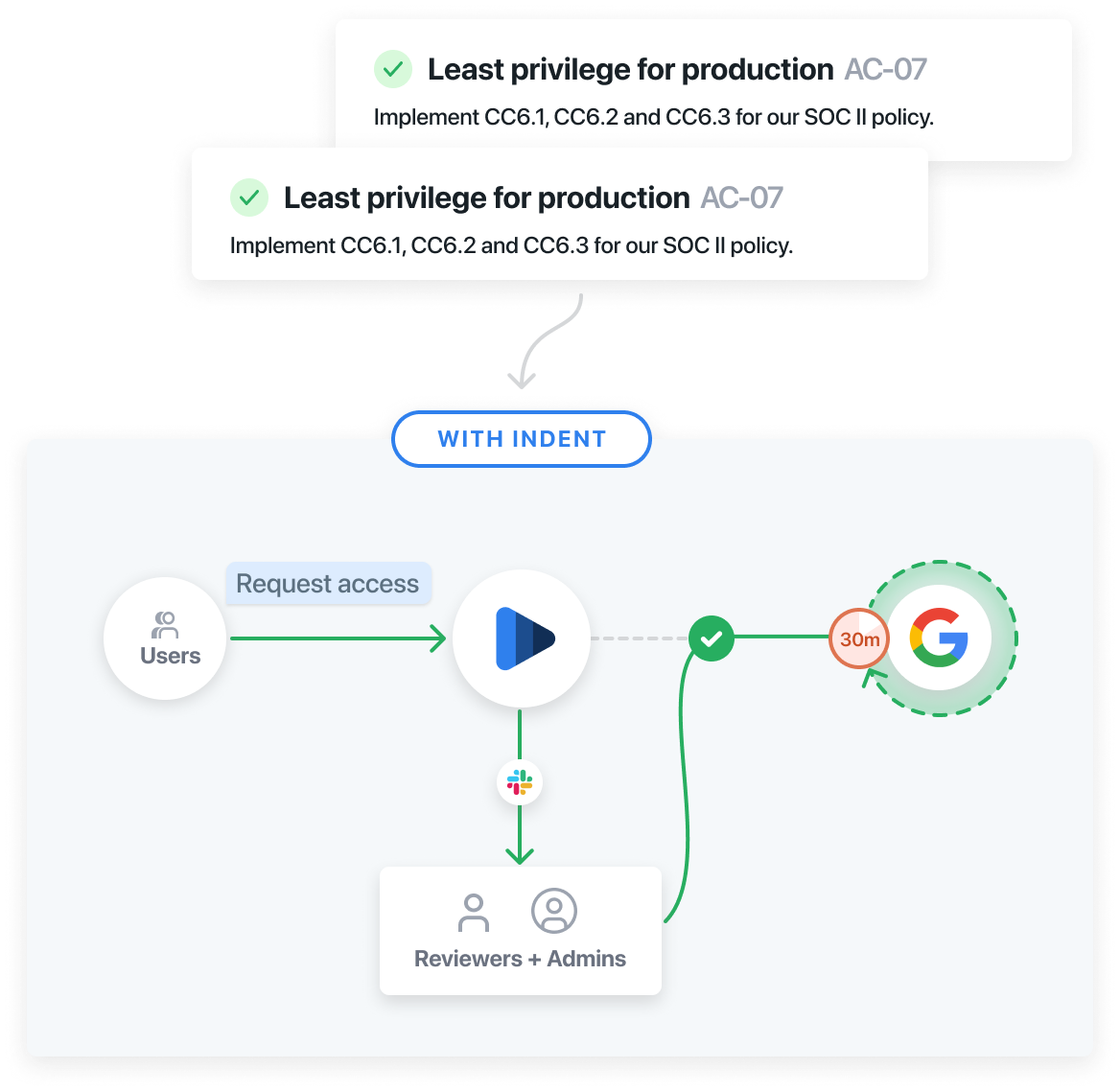
- For Operations: protect against breaches with least privilege and access reviews to easily produce audit reports

Stevan Arychuk
Head of InfoSec & SRE

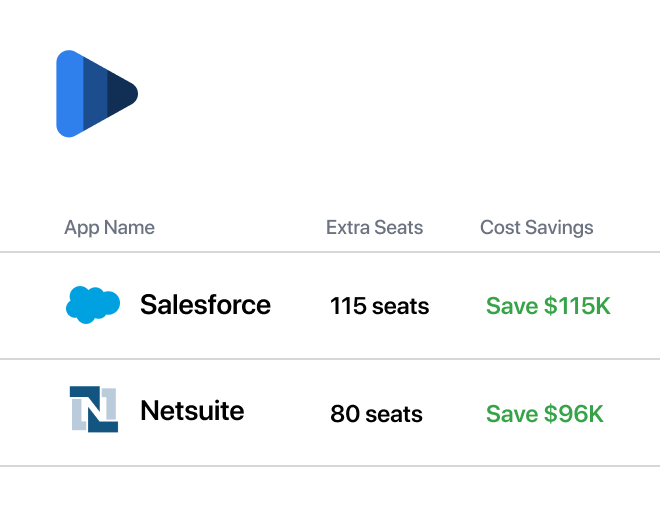
Cut costs, not corners with on-demand floating licenses.

Becky Vredenburg
IT Ops Engineer

Turn security and compliance controls into effortless policies.

Geoff Harcourt
CTO, Co-Founder

Trusted by forward-thinking companies
Protect your cloud, apps, and customer data without disrupting your team's workflows.